Oh great: New attack makes some password cracking faster, ea
Source: Dan Goodin
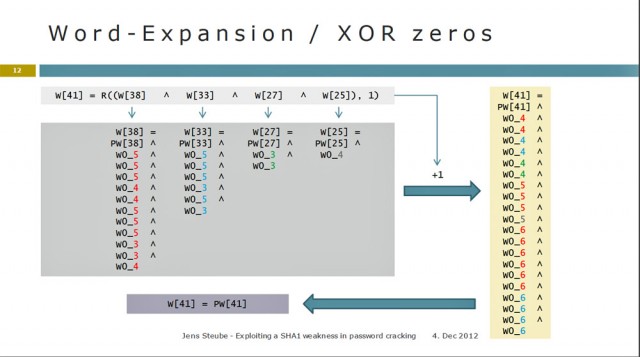 A slide from Steube's presentation outlining a more efficient way to crack passwords protected by the SHA1 cryptographic algorithm.
A slide from Steube's presentation outlining a more efficient way to crack passwords protected by the SHA1 cryptographic algorithm.
hashcat.net
A researcher has devised a method that reduces the time and resources required to crack passwords that are protected by the SHA1 cryptographic algorithm.
The optimization, presented on Tuesday at the Passwords^12 conference in Oslo, Norway, can speed up password cracking by 21 percent. The optimization works by reducing the number of steps required to calculate SHA1 hashes, which are used to cryptographically represent strings of text so passwords aren't stored as plain text. Such one-way hashes―for example 5baa61e4c9b93f3f0682250b6cf8331b7ee68fd8 to represent "password" (minus the quotes) and e38ad214943daad1d64c102faec29de4afe9da3d for "password1"―can't be mathematically unscrambled, so the only way to reverse one is to run plaintext guesses through the same cryptographic function until an identical hash is generated.
Jens Steube―who is better known as Atom, as the pseudonymous developer of the popular Hashcat password-recovery program―figured out a way to remove identical computations that are performed multiple times from the process of generating of SHA1 hashes. By precalculating several steps ahead of time, he's able to skip the redundant steps, shaving 21 percent of the time required to crack large numbers of passwords. Slides from Tuesday's presentation are here.
"This technique reduces the computational cost of testing candidate passwords when one is given the SHA1 hash of an unknown password," Jean-Philippe Aumasson, a Switzerland-based cryptography expert, wrote in an e-mail to Ars. "In mathematical terms, it does so by avoiding redundant operations―that is, operations that have to be performed regardless of the password tested."
Aumasson is the main designer of BLAKE, one of five finalist hash functions in the competition to designate the SHA3 algorithm. In October, it was edged out by another finalist function known as Keccak.
The optimization is only the latest reason architects of websites and networks should abandon SHA1 for password hashing. As Ars explained in a recent featured headlined Why passwords have never been weaker―and crackers have never been stronger, SHA1, MD5, and a variety of other algorithms widely used to protect passwords are grossly unsuited to the job because they were designed to generate hashes quickly using a minimal amount of computing resources. Underscoring the weakness of SHA1 was the June release of 6.5 million LinkedIn password hashes.
Because SHA1 uses a single iteration to generate hashes, it took security researcher Jeremi Gosney just six days to crack 90 percent of the list. Had the same passwords been hashed using an algorithm specifically designed to protect passwords―algorithms such as Bcrypt, PBKDF2, or SHA512crypt―it would have taken Gosney years or even centuries to accomplish the same feat. The latter three hashes are better suited to password storage because they require significantly more time and computation to convert plaintext into hashes.
"Note that using SHA1 for password storage (with or without a 'salt') is not a very good practice anyway," Aumasson wrote.
Steube's research is only the latest method for speeding up the process of generating SHA1 hashes. The official SHA1 specification calls for 1,448 distinct steps to calculate a hash. Before now, Gosney said, crackers had already figured out how to reduce the number to 1,372, and by using special hardware instructions supported by graphics cards manufactured by AMD, many crackers were further able to cut the steps to 868.
"This is where we have been for a few years now, and we all thought this was pretty damn good," Gosney told Ars.
Steube's optimization cuts an additional 134 steps out of the SHA1 hashing process. The method works by eliminating XOR logical operations during the expansion phase of generating a SHA1 hash. Expansion acts as an amplifier of sorts that allows a hash to contain more data than is found in the originating plaintext. Because many of the steps in the process don't rely on the plaintext, they can be carried out using precalculated data.
A 21 percent optimization is impressive, but it's modest when compared with the password-cracking gains that have been achieved in the past few years. The use of graphics cards alone allows inexpensive computers to work thousands of times faster than they did just a decade ago on similarly priced PCs that used traditional CPUs alone. As a result, a PC running a single AMD Radeon HD7970 GPU can try on average 8.2 billion password combinations each second, depending on the algorithm used to protect them. So while the technique unveiled on Tuesday is impressive, it's important to put it in perspective, cracking experts said.
"I don't want to downplay 20 percent, which is significant," Rob Graham, CEO of penetration testing firm Errata Security, told Ars. "But it's not on the order of, say, switching from a CPU to a GPU."
| }
|