How the KRACK attack destroys nearly all Wi-Fi security
Source: KRACKATOA
 A paper by two Belgian researchers has cast more light on the vulnerabilities discovered in the Wi-Fi Protected Access II (WPA2) implementations on most, if not all, wireless networking devices that use the protocol. Dubbed "KRACK" (Key Reinstallation AttaCK), the attack "abuses design or implementation flaws in cryptographic protocols to reinstall an already-in-use key," wrote Mathy Vanhoef and Frank Piessens of the Katholieke Universiteit Leuven (KU Leuven) in the paper, released today.
A paper by two Belgian researchers has cast more light on the vulnerabilities discovered in the Wi-Fi Protected Access II (WPA2) implementations on most, if not all, wireless networking devices that use the protocol. Dubbed "KRACK" (Key Reinstallation AttaCK), the attack "abuses design or implementation flaws in cryptographic protocols to reinstall an already-in-use key," wrote Mathy Vanhoef and Frank Piessens of the Katholieke Universiteit Leuven (KU Leuven) in the paper, released today.
The report came after wide disclosure of the problems, as Ars reported Sunday night. The research is built upon previous explorations of weaknesses in WPA2's component protocols, and some of the attacks mentioned in the paper were previously acknowledged to be theoretically possible. However, the authors have turned these vulnerabilities into proof-of-concept code, "and found that every Wi-Fi device is vulnerable to some variant of our attacks. Notably, our attack is exceptionally devastating against Android 6.0: it forces the client into using a predictable all-zero encryption key."
While Windows and iOS devices are immune to one flavor of the attack, they are susceptible to others. And all major operating systems are vulnerable to at least one form of the KRACK attack. And in an addendum posted today, the researchers noted that things are worse than they appeared at the time the paper was written:
Although this paper is made public now, it was already submitted for review on 19 May 2017. After this, only minor changes were made. As a result, the findings in the paper are already several months old. In the meantime, we have found easier techniques to carry out our key reinstallation attack against the 4-way handshake. With our novel attack technique, it is now trivial to exploit implementations that only accept encrypted retransmissions of message 3 of the 4-way handshake. In particular this means that attacking macOS and OpenBSD is significantly easier than discussed in the paper.
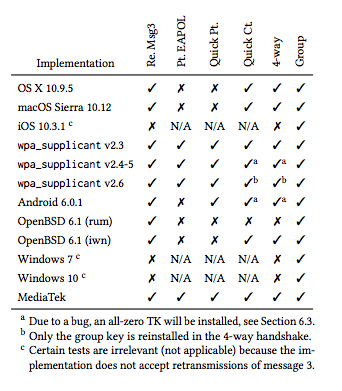
Everything is vulnerable to at least one kind of attack, according to Vanhoef and Piessens.
Wi-Fi networks typically use shared keys (usually based on AES encryption) to protect network traffic. That key is shared via a collection of cryptographic "handshakes" that verify the identity of network clients. The attack style documented by Vanhoef and Piessens targets those cryptographic handshakes: the four-way handshake used to initially pass a shared key to the client or the PeerKey Handshake used in peer-to-peer network connections; the group key refresh handshake used by the network to change the key when a client leaves the network; and the Fast Basic Service Set (BSS) Transition (FT) handshake used to allow clients to roam around a network with multiple access points.
Further Reading
Even with a VPN, open Wi-Fi exposes users
While Windows and Apple IOS devices are not vulnerable to the four-way handshake attack, they are vulnerable to the group key handshake attack and the Fast BSS attack. Android 6.0, Chromium, and Android Wear 2.0 devices are particularly vulnerable to four-way handshake attacks—an attack actually causes the protocol to reinstall a predictable, all-zero key, making it trivial to decrypt the network's traffic. The same is true of other Linux implementations that use version 2.4 and 2.5 of wpa_supplicant, the Wi-Fi client commonly used on Linux (wpa_supplicant's most recent version is 2.6).
"This vulnerability appears to be caused by a remark in the 802.11 standard that suggests to clear parts of the session key from memory once it has been installed," Vanhoef and Piessens explained. "As a result, currently 31.2 percent of Android devices are vulnerable to this exceptionally devastating variant of our attack."
In an addendum to the paper posted by the authors today, Vanhoef and Piessens expanded on their results, expanding the problem to all current Linux distributions:
Linux's wpa_supplicant v2.6 is also vulnerable to the installation of an all-zero encryption key in the 4-way handshake. This was discovered by John A. Van Boxtel. As a result, all Android versions higher than 6.0 are also affected by the attack, and hence can be tricked into installing an all-zero encryption key. The new attack works by injecting a forged message 1, with the same ANonce as used in the original message 1, before forwarding the retransmitted message 3 to the victim. In each case, the attacker can force a targeted device to re-install an already-in-use shared key, downgrading the key.
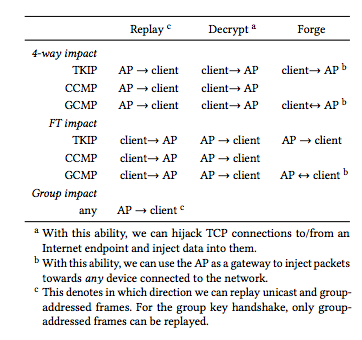
The flavors of KRACK pain.
Vanhoef and Piessens
Depending on the type of handshake being used between the nodes on the Wi-Fi network, the attack can do varying levels of damage:
For connections using AES and the Counter with CBC-MAC Protocol ((AES)-CCMP), an attacker can decrypt network packets, making it possible to read their contents and to inject malicious content into TCP packet streams. But the key itself cannot be broken or forged, so the attacker can't forge a key and join the network—instead, they have to use a "cloned" access point that uses the same MAC address as the access point of the targeted network, on a different Wi-Fi channel.
For WPA2 systems using the Temporal Key Integrity Protocol (TKIP), the Message Integrity Code key can be recovered by the attacker. This allows them to replay captured packets to the network; they can also forge and transmit new packets to the targeted client posing as the access point.
For devices that use the Galois/Counter Mode Protocol (GCMP), the attack is the worst: "It is possible to replay and decrypt packets," Vanhoef and Piessens wrote. "Additionally, it is possible to recover the authentication key, which in GCMP is used to protect both communication directions [as client or access point]… therefore, unlike with TKIP, an adversary can forge packets in both directions." That means that the attacker can essentially join the network and pretend to be a client or the access point, depending on the type of access they want. "Given that GCMP is expected to be adopted at a high rate in the next few years under the WiGig name, this is a worrying situation," the researchers noted.
| }
|