UK-promoted phone crypto scheme “facilitates undetectable ma
Source: Dan Goodin
 A security scheme that Britain's spy agency is promoting for encrypting phone calls contains a backdoor that can be accessed by anyone in possession of a master key, according to an analysis published Tuesday by a security expert at University College in London.
A security scheme that Britain's spy agency is promoting for encrypting phone calls contains a backdoor that can be accessed by anyone in possession of a master key, according to an analysis published Tuesday by a security expert at University College in London.
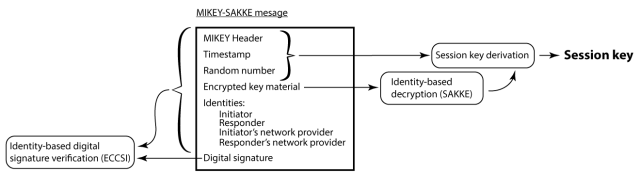
The MIKEY-SAKKE protocol is a specification based on the Secure Chorus, an encryption standard for voice and video that was developed by the Communications Electronics Security Group, the information security arm of the UK's Government Communications Headquarters. British governmental officials have indicated that they plan to certify voice encryption products only if they implement MIKEY-SAKKE and Secure Chorus.
According to Steven J. Murdoch, a Royal Society University Research Fellow in the Information Security Research Group of University College, MIKEY-SAKKE contains a backdoor that allows communications to be decrypted in bulk. It can be activated by anyone who has access to a master private key that's responsible for generating intermediate private keys. Because the master key is required to create new keys and to update existing ones, network providers must keep the master key permanently available.
"The existence of a master private key that can decrypt all calls past and present without detection, on a computer permanently available, creates a huge security risk, and an irresistible target for attackers," Murdoch wrote in the analysis titled "Insecure by design: protocols for encrypted phone calls." "Also calls which cross different network providers (e.g., between different companies) would be decrypted at a gateway computer, creating another location where calls could be eavesdropped."
Murdoch went on to characterize the scheme as part of a key escrow that allows government agents to obtain the individual encryption keys that were generated using the master key. "Secure Chorus facilitates undetectable mass surveillance, in a way that [much more secure Ephemeral Diffie-Hellman]-based key encryption schemes would not. This is presented as a feature rather than bug, with the motivating case in the GCHQ documentation being to allow companies to listen to their employees calls when investigating misconduct, such as in the financial industry."
In the 1990s, the US government waged a similar campaign to build key-escrow capabilities into widely used encryption schemes. More recently, US officials have sometimes criticized Google, Apple, and other companies for providing default encryption capabilities that have the potential to thwart criminal or national security investigations.
| }
|